pfSenseをアップデートした記録 2.5.0→2.5.1
アップデート内容確認
2.5.0から2.5.1にアップデートします
変更点を確認
https://docs.netgate.com/pfsense/en/latest/releases/21-02-2_2-5-1.html
Known Issues / Errata
There is an issue with AES-NI hash acceleration for SHA1 and SHA-256. If the AES-NI driver detects a system capable of accelerating SHA1 or SHA-256 and the firewall attempts to utilize one of those hashes, the affected operation may fail. This affects IPsec and OpenVPN, among other uses. pfSense Plus users can change to QAT acceleration on supported hardware instead. In cases where QAT is unavailable, change to AES-GCM, change to a different unaccelerated hash (e.g. SHA-512), or disable AES-NI. See #11524 for details.
There is a similar issue which affects SafeXcel SHA1 and SHA2 hash acceleration on SG-1100 and SG-2100. On that hardware, change to an AEAD cipher such as AES-GCM or switch to an unaccelerated hash. This issue is being tracked internally on NG #6005
The FRR package on pfSense Plus 21.02 and pfSense CE 2.5.0 and later no longer exchanges routes with BGP peers by default without being explicitly allowed to do so. This is more secure behavior but requires a manual change. To replicate the previous behavior, add a route map to permit all routes (Name: allow-all, Action: Permit, Sequence: 100), then set that route map on BGP neighbors for inbound and outbound peer filtering. For increased security, utilize route maps which filter incoming and outgoing routes so they match more strictly. See Peer Filtering and BGP Example Configuration for more information.
pfSense Plus
Certificates
Fixed: CA and certificate validity end dates after 2038 are not handled properly on 32-bit ARM #11504
Interfaces
Added: Interface Status page information for switch uplinks may be replaced by switch port data when media state monitoring is set #10804
Rules / NAT
Fixed: State matching problem with reponses to packets arriving on non-default WANs #11436
Upgrade
Fixed: LEDs do not indicate available upgrade status #11689
pfSense CE
Aliases / Tables
Fixed: Alias name change is not reflected in firewall rules #11568
Authentication
Fixed: Unreachable LDAP server for SSH auth causes boot process to stop at at ‘Synchronizing user settings’ and no user can login over SSH #11644
Certificates
Fixed: Invalid certificate data can cause a PHP error #11489
Fixed: Renewing a self-signed CA or certificate does not update the serial number #11514
Fixed: Unable to renew a certificate without a SAN #11652
Fixed: Certificates with escaped x509 characters display the escaped version when renewing #11654
Fixed: Creating a certificate while creating a user does not fully configure the certificate properly #11705
Fixed: Renewing a certificate without a type value assumes a server certificate #11706
DNS Resolver
Fixed: DNS Resolver does not add a local-zone type for ip6.arpa domain override #11403
Fixed: DNS Resolver does not bind to an interface when it recovers from a down state #11547
Dashboard
Fixed: CPU details are incorrect in the System Information widget after resetting log files #11428
Fixed: Disabling ‘State Table Size’ in the System Information widget prevents other data from being displayed #11443
Gateway Monitoring
Fixed: Automatic default gateway mode does not select expected entries #11729
Gateways
Fixed: Gateways with “Use non-local gateway” set are not added to routing table #11433
IPsec
Fixed: IPsec status incorrect for entries using expanded IKE connection numbers #11435
Fixed: Distinguished Name (FQDN) IPsec peer identifier type is not formatted properly in swanctl.conf secrets #11442
Fixed: Mobile IPsec DNS server input validation does not reject unsupported IPv4-mapped IPv6 addresses #11446
Fixed: Broken help link on IPsec Advanced Settings tab #11474
Fixed: Connect and disconnect buttons on the IPsec status page do not work for all tunnels #11486
Fixed: IPsec tunnels using expanded IKE connection numbers do not have proper child SA names in swanctl.conf #11487
Fixed: IPsec tunnel definitions have pools = entry in swanctl.conf with no value #11488
Fixed: Mobile IPsec broken when using strict certificate revocation list checking #11526
Fixed: IPsec VTI tunnel between IPv6 peers may not configure correctly #11537
Fixed: IPsec peer ID of “Any” does not generate a proper remote definition or related secrets #11555
Fixed: IPsec tunnel does not function when configured on a 6RD interface #11643
IPv6 Router Advertisements (RADVD)
Fixed: IPv6 RA RDNSS lifetime is too short, not compliant with RFC 8106 #11105
Installer
Fixed: Installer does not add required module to loader.conf when using ZFS #11483
Interfaces
Fixed: IPv4 MSS value is incorrectly applied to IPv6 packets #11409
Fixed: Gateway value for DHCP6 interfaces missing after RA events triggered script without gateway information #11454
Fixed: Delayed packet transmission in cxgbe driver can lead to latency and reduced performance #11602
Fixed: DHCP6 interfaces are reconfigured multiple times at boot when more than one interface is set to Track #11633
Logging
Fixed: Entries from rotated log files may be displayed out of order when log display includes contents from multiple files #11639
Notifications
Fixed: Telegram and Pushover notification API calls do not respect proxy configuration #11476
OpenVPN
Fixed: OpenVPN authentication and certificate validation fail due to size of data passed through fcgicli #4521
Added: Display negotiated data encryption algorithm in OpenVPN connection status #7077
Fixed: OpenVPN does not start with several authentication sources selected #11104
Fixed: OpenVPN client configuration page displays Shared Key option when set for SSL/TLS #11382
Fixed: Incorrect order of route-nopull option in OpenVPN client-specific override configuration #11448
Fixed: OpenVPN using the wrong OpenSSL command to list digest algorithms #11500
Fixed: Selected Data Encryption Algorithms list items reset when an input validation error occurs #11554
Fixed: OpenVPN does not start with a long list of Data Encryption Algorithms #11559
Fixed: ACLs generated from RADIUS reply attributes do not parse {clientip} macro #11561
Fixed: ACLs generated from RADIUS reply attributes have incorrect syntax #11569
Fixed: OpenVPN binds to all interfaces when configured on a 6RD interface #11674
Operating System
Fixed: Unexpected Operator error on console at boot with ZFS and RAM Disks #11617
Changed: Upgrade OpenSSL to 1.1.1k #11755
Routing
Fixed: Disabled static route entries trigger ‘route delete’ error at boot #3709
Fixed: Route tables with many entries can lead to PHP errors and timeouts when looking up routes #11475
Fixed: Error when removing automatic DNS server route #11578
Fixed: IPv6 routes with a prefix length of 128 result in an invalid route table entry #11594
Fixed: Error when deleting IPv6 link-local routes #11713
Rules / NAT
Fixed: Saved state timeout values not loaded into GUI fields on system_advanced_firewall.php #11565
Fixed: Firewall rule schedule cannot be changed #11747
Upgrade
Fixed: pfSense Proxy Authentication not working #11383
Wake on LAN
Fixed: Potential stored XSS vulnerability in services_wol.php #11616
Web Interface
Fixed: Requests to ews.netgate.com do not honor proxy configuration #11464
XMLRPC
Fixed: XMLRPC error with Captive Portal and CARP failover when GUI is on non-standard port #11425
Fixed: Incorrect DHCP failover IP address configured on peer after XMLRPC sync #11519
Fixed: PHP error in logs from XMLRPC if no sections are selected to sync #11638
今回は修正メインのアップデートで
更新パッケージも少なく、短時間で完了しました
大きなポイントとしては2.5.0で導入されたWireGuardが
今回の2.5.1で削除されていますので
WireGuardを有効にしていた場合は無効設定に変更してから
2.5.1へアップデートすることが推奨されています
WireGuardについてはNetgateがMatthew Macyに依頼し
ベースOSであるFreeBSDにWireGuardをカーネル実装しようとしていたのですが
どうやらその移植されたソースコードがかなりの問題作だったようです
細かい情報が気になる方は「Matthew Macy WireGuard」で検索
結果的にはFreeBSD 13.0-RELEASEでの実装計画はキャンセルとなりましたが
Matthew MacyではなくWireGuardを開発したJason A. Donenfeld自身が
カーネル実装を表明したりしているので方針自体は継続しており
現時点ではFreeBSD 13.xでの実装を予定されておりますので
いずれpfSenseでもWireGuardが利用できる日がくると思われます
[ANNOUNCE] WireGuard for FreeBSD in development for 13.y – and a note of how we got here
https://lists.zx2c4.com/pipermail/wireguard/2021-March/006494.html
あと既知の問題にある通り、2.5系においてAES-NI利用に不具合が確認されています
SHA1とSHA-256を使ったIPsec・OpenVPNを利用している場合は注意してください
2.5系を利用している場合の回避策は
SHA-512にするかAES-GCMにするかAES-NI無効の3択です
私の環境はOpenVPNを利用していましたが
元々AES-GCMを利用していたので特に影響はなく
2.5.1でも問題なく利用できています
アップデートの手順
今回もpfSense CEでのアップデートです
事前に設定のバックアップをした上で以下の操作でアップデートを実行
手順はいつもと同じです
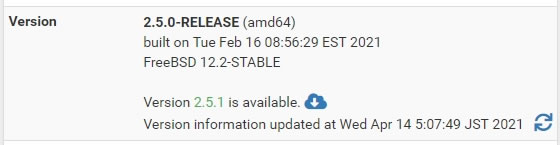
2.5.0から2.5.1へアップデートと表示出てるのを確認して「Confirm」を押す
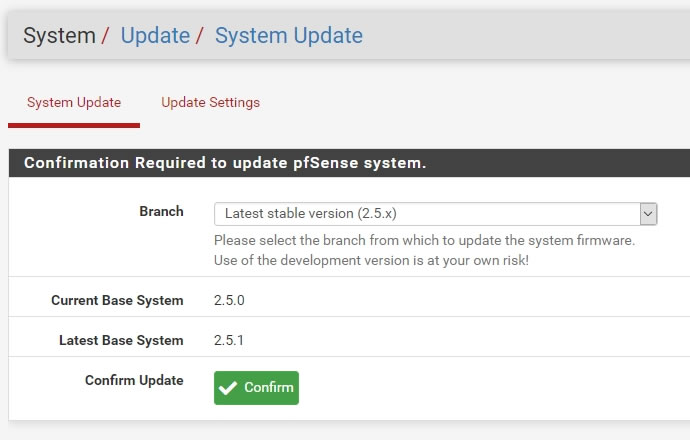
Update時の処理ログ
>>> Updating repositories metadata...
Updating pfSense-core repository catalogue...
Fetching meta.conf: . done
Fetching packagesite.txz: . done
Processing entries: . done
pfSense-core repository update completed. 7 packages processed.
Updating pfSense repository catalogue...
Fetching meta.conf: . done
Fetching packagesite.txz: .......... done
Processing entries: .......... done
pfSense repository update completed. 508 packages processed.
All repositories are up to date.
>>> Removing vital flag from php74... done.
>>> Downloading upgrade packages...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Checking for upgrades (9 candidates): ......... done
Processing candidates (9 candidates): ......... done
The following 9 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
bind-tools: 9.16.11 -> 9.16.12 [pfSense]
nettle: 3.6 -> 3.7.2_1 [pfSense]
openvpn: 2.5.0 -> 2.5.1 [pfSense]
pfSense: 2.5.0 -> 2.5.1 [pfSense]
pfSense-base: 2.5.0 -> 2.5.1 [pfSense-core]
pfSense-default-config: 2.5.0 -> 2.5.1 [pfSense-core]
pfSense-kernel-pfSense: 2.5.0 -> 2.5.1 [pfSense-core]
pfSense-rc: 2.5.0 -> 2.5.1 [pfSense-core]
unbound: 1.13.0_2 -> 1.13.1 [pfSense]
Number of packages to be upgraded: 9
95 MiB to be downloaded.
[1/9] Fetching unbound-1.13.1.txz: .......... done
[2/9] Fetching pfSense-rc-2.5.1.txz: .. done
[3/9] Fetching pfSense-kernel-pfSense-2.5.1.txz: .......... done
[4/9] Fetching pfSense-default-config-2.5.1.txz: . done
[5/9] Fetching pfSense-base-2.5.1.txz: .......... done
[6/9] Fetching pfSense-2.5.1.txz: . done
[7/9] Fetching openvpn-2.5.1.txz: .......... done
[8/9] Fetching nettle-3.7.2_1.txz: .......... done
[9/9] Fetching bind-tools-9.16.12.txz: .......... done
Checking integrity... done (0 conflicting)
>>> Downloading pkg...
The following packages will be fetched:
New packages to be FETCHED:
pkg: 1.16.1 (7 MiB: 100.00% of the 7 MiB to download)
Number of packages to be fetched: 1
The process will require 7 MiB more space.
7 MiB to be downloaded.
Fetching pkg-1.16.1.txz: .......... done
>>> Upgrading pfSense-rc...
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pfSense-rc: 2.5.0 -> 2.5.1 [pfSense-core]
Number of packages to be upgraded: 1
[1/1] Upgrading pfSense-rc from 2.5.0 to 2.5.1...
===> Setting net.pf.request_maxcount=400000
[1/1] Extracting pfSense-rc-2.5.1: ...... done
>>> Upgrading pfSense kernel...
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pfSense-kernel-pfSense: 2.5.0 -> 2.5.1 [pfSense-core]
Number of packages to be upgraded: 1
[1/1] Upgrading pfSense-kernel-pfSense from 2.5.0 to 2.5.1...
[1/1] Extracting pfSense-kernel-pfSense-2.5.1: .......... done
===> Keeping a copy of current kernel in /boot/kernel.old
>>> Removing unnecessary packages... done.
System is going to be upgraded. Rebooting in 10 seconds.
Success


コメント