pfSense CEをアップデートした記録 2.7.0→2.7.1
アップデート内容確認
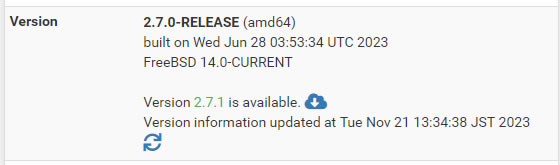
pfSense CE 2.7.0からpfSense CE 2.7.1にアップデートします
変更点を確認
https://docs.netgate.com/pfsense/en/latest/releases/2-7-1.html
General
PHP has been upgraded to 8.2.11
The base operating system has been upgraded to a more recent point on FreeBSD 14-CURRENT
Support for SCTP has been improved in PF for firewall rules, NAT, and logging. Rules can now act on SCTP packets by port number, previously it was only possible to filter on source or destination address.
OpenSSL in the base system has been upgraded from 1.1.1t to 3.0.12.
Kea DHCP Server has been added as an opt-in feature preview for IPv4 and IPv6 DHCP service. Kea will eventually replace the ISC DHCPD daemon which is EOL.
Warning
Kea is not yet feature complete. For details, see Kea DHCP Server feature preview now available.
IPv6 Router Advertisement configuration has been relocated to Services > Router Advertisement as a part of the ongoing DHCP Server changes.
Certain parts of the base system are being migrated to packages rather than grouping them all together in an archive in the “base” package. For the most part this should be entirely transparent to users.
Specifically, the code from the main pfSense software repository is now a part of the “pfSense” package. This lets management of files be handled entirely by pkg rather than carrying them in an archive. This migration is ongoing, so future versions will include additional portions of the system being packaged differently.
The default driver for NVMe storage devices changed from nvd(4) to nda(4). For most users this will be a transparent change since the majority of installations are mounted by label and do not reference a storage device by name.
Some swap configurations may reference the old device name in /etc/fstab. Editing that file and correcting device names from nvd to nda, followed by a reboot, should restore swap functionality.
If the new driver is problematic in certain environments the default can be changed back to nvd(4) by adding a loader tunable for hw.nvme.use_nvd=1.
Troubleshooting
Due to changes in pkg, the new version of pkg may not be able to properly locate and use the CA trust store when running on the previous version before upgrading.
If the firewall is unable to load packages or check for updates after selecting the CE 2.7.1 upgrade branch, run certctl rehash from the console, a root shell prompt, or via Diagnostics > Command Prompt. This will allow pkg to utilize the system certificates until the next reboot.
OpenSSL upgraded to 3.0.12
OpenSSL has been upgraded to 3.0.12 from 1.1.1 in FreeBSD.
This change was necessary as OpenSSL 1.1.1 reached its End of Life (EOL) on September 11, 2023. This means there will be no security patches for vulnerabilities affecting OpenSSL 1.1.1.
The OpenSSL team decided to make an explicit jump in numbering from 1.1.x to 3.x to highlight that this new version included major structural, and more importantly, application programming interface (API) and application binary interface (ABI) changes compared to previous OpenSSL versions.
In addition to the differences in the library they also deprecated numerous weak algorithms of various types.
Due to these differences, changing from OpenSSL 1.1 to OpenSSL 3.0 is not a simple upgrade. Netgate developers have handled most of these changes as automatically as possible, though some things may still require manual adjustments. See the warnings in the next section for details.
OpenSSL 3.0.x Upgrade Warnings
Weak Certificate Digests such as SHA1 are Deprecated
Warning
OpenSSL 3.0.x no longer supports certificates signed with SHA1 or other older/weaker hashes. The minimum recommended hash strength is SHA256.
The upgrade process detects usage of weak certificates for the GUI, Captive Portal, and OpenVPN:
If the GUI or a Captive Portal zone utilizes a weak CA or server certificate, the upgrade process generates a new self-signed certificate as a stopgap measure to allow the processes to start and let the user in to make any necessary corrections.
If an OpenVPN instance is using a weak certificate, the instance is disabled as there is no viable general automated recovery method.
OpenVPN peers using SHA1 certificates will fail, but such issues must be corrected on the peers. This may mean renewing or reissuing certificates or re-exporting clients for peers if they are currently using weak certificates.
Other consumers of certificates, such as add-on packages, may be similarly affected but cannot be automatically adjusted.
The best practice is to reconfigure all services utilizing certificates with stronger certificates and to test these functions before performing an upgrade to ensure a smoother transition.
Numerous Deprecated Encryption and Digest Algorithms Removed
Warning
OpenSSL 3.0.x removes a large number of deprecated encryption and digest algorithms. This primarily affects OpenVPN, as other areas had not supported the affected algorithms in some time.
Encryption algorithms removed from OpenVPN:
ARIA
Blowfish (e.g. BF-CBC), which was formerly an OpenVPN default
CAST5
DES
DESX
IDEA
RC2
RC5
SEED
SM4
Hash algorithms removed from OpenVPN:
MD4
MDC2
SM3
Whirlpool
On upgrade, tunnels using these deprecated algorithms will be adjusted so they use more secure default values when necessary.
The best practice is to reconfigure tunnels using modern secure encryption and hashing, and to test tunnels before performing an upgrade to ensure a smoother transition.
Other OpenSSL-Related Concerns
The certificate manager in the GUI can still read and generate certificates using weak hashes, but warns against their use. Avoid creating any new entries using weak hashes. This support will eventually be removed.
The certificate manager no longer supports importing PKCS#12 archive files which were encrypted with weak ciphers, such as RC2-40. Some operating systems still export using such weak ciphers by default, including macOS and Windows.
IPsec does not require any adjustments, it still supports SHA1 certificates for the time being and no additional algorithms have been deprecated or removed.
Unbound does not require any adjustments, it still supports SHA1 certificates for the time being.
Though the legacy provider for OpenSSL 3.0.x is built and included it does not help to work around the issues mentioned above in any meaningful way.
Kea DHCP Server feature preview now available
The ISC DHCPD server has reached its End of Life (EOL) as of October 5, 2022. Though ISC has stated they may continue to publish security fixes if they are warranted.
Netgate developers have started the migration to Kea DHCP server from ISC as a replacement for ISC DHCPD for IPv4 and IPv6 DHCP service. Basic functionality is present, but not all features are supported at this time.
Warning
Currently the Kea implementation lacks the following DHCP server features:
Local DNS Resolver/Forwarder Registration for static and dynamic DHCP clients
Remote DNS server registration
DHCPv6 Prefix Delegation
High Availability Failover
Lease statistics/graphs
Custom DHCP options
Kea is available as an opt-in preview feature on this release. The UI and settings for Kea are shared with the existing DHCP server. Administrators can easily switch between ISC DHCPD and Kea by navigating to System > Advanced, Networking tab and changing the new Server Backend setting in the DHCP Options section.
After Kea integration is complete it will become the default DHCP server on a future release of pfSense software and eventually the deprecated ISC DHCP server will be removed. The exact timing of these changes has not been finalized.
Note
As a part of changes to the DHCP server, IPv6 Router Advertisement configuration has been separated from the DHCP server UI and relocated to Services > Router Advertisement.
Security
In addition to OpenSSL and other concerns in the base OS and packages, this release addresses the following vulnerabilities in pfSense software:
pfSense-SA-23_08.webgui (XSS in getserviceproviders.php, #14547)
pfSense-SA-23_09.webgui (XSS in status_logs_filter_dynamic.php, #14548)
pfSense-SA-23_10.webgui (Authenticated Command Execution in interfaces_gif_edit.php and interfaces_gre_edit.php, #14549)
pfSense-SA-23_11.webgui (Authenticated Command Execution in packet_capture.php, #14809)
Tip
Patches for these issues are also available in the latest version of the System Patches Package for users of pfSense Plus software version 23.05.1 and pfSense CE software version 2.7.0.
pfSense CE
Changes in this version of pfSense CE software.
Aliases / Tables
Fixed: Firewall rules fail to load when a URL table alias file does not exist #13068
Added: Type column on Alias lists #13245
Fixed: Static ARP entries are not configured at boot #14374
Fixed: Firewall rules are not displayed properly when they reference a URL table alias and its file does not exist #14574
Authentication
Added: Option to invalidate GUI login session if the client address changes #14265
Backup / Restore
Changed: Increase timeout for password entry when restoring an encrypted configuration via ECL #14769
CARP
Added: Prevent CARP status/maintenance mode from being erroneously toggled #13804
Fixed: IPsec restart in CARP event scripts does not check VIP properly and never runs #14738
Captive Portal
Fixed: Captive Portal incorrectly allows leading zeroes on voucher roll numbers #14325
Fixed: Link to view Captive Portal custom HTML page content does not work #14598
Certificates
Fixed: Cannot validate Certificates against Certificate Revocation Lists for Intermediate Certificate Authorities #9889
Added: Improve System menu behavior for Certificate Manager privileges #14347
Fixed: CA and Certificate renewal page does not properly list some SHA1 certificates as being weak #14678
Console Menu
Fixed: PHP shell script pfanchordrill shows duplicate anchor content #14637
DHCP (IPv4)
Added: Introduce Kea DHCP as an alternative DHCP server for IPv4 and IPv6 #6960
DNS Resolver
Added: Unbound Advanced Settings entry for sock-queue-timeout #14731
Changed: Update Unbound to 1.18.0_1 to address looping UDP retries when ENOBUFS is returned #14980
Dashboard
Fixed: System Information widget does not properly form list of active hardware crypto algorithms #14417
Fixed: Gateway widget tooltip incorrectly indicates some gateways as being default #14542
Diagnostics
Fixed: diag_edit.php warning is not cleared after picking non-directory to load #7589
Changed: Combining Interface and Rule ID state table filter fields returns no results #14399
Fixed: Improve error handling in status.php #14513
Added: Status output plugin hook for packages to include their own data #14777
Dynamic DNS
Added: Include hostname being updated in Dynamic DNS notifications #9504
Added: Dynamic DNS support for Porkbun #14402
Fixed: PHP error with One.com Dynamic DNS provider #14649
Fixed: List of Dynamic DNS types with split host+domain name is missing several providers #14783
Fixed: Correct name of Gandi LiveDNS #14784
Fixed: Multi-WAN Dynamic DNS does not fail over when preferred WAN loses link #14829
Gateways
Fixed: Misleading error message when adding/editing static routes which use a gateway on a disabled interface #8846
Fixed: Cannot select IP Alias VIP with CARP VIP parent in Virtual IP drop-down on Gateway Groups #14524
Fixed: A default route can remain after setting the default gateway to None #14717
Hardware / Drivers
Fixed: Unnecessary delay when querying ixgbe(4) interfaces with SFP ports #13911
Added: Options to control Intel Speed Shift #14047
Fixed: Cavium qlnxe / if_qlnxe driver is not present #14534
Fixed: bnxt(4) driver errors #14569
Added: QAT 200xx devices are not recognized as supported #14844
IGMP Proxy
Fixed: Input validation error when saving IGMP Proxy settings #14301
Fixed: IGMP Proxy cannot start on VirtIO (vtnet) interfaces #14665
IPsec
Changed: Clarify that the IPsec keep alive check option ignores Child SA Start Action #12762
Fixed: PHP error in status_ipsec.php after removing active IPsec tunnel configuration #14525
Fixed: Multi-WAN IPsec does not fail over when preferred WAN loses link #14626
Added: Show IPsec phase 1 authentication type in Mode column of tunnel list #14726
Fixed: IPsec rejects certificate without any SANs #14831
IPv6 Router Advertisements (radvd/rtsold)
Fixed: IPv6 neighbor discovery protocol (NDP) fails in some cases #13423
Interfaces
Fixed: GIF-based interface MTU is assigned to parent interface on boot when parent interface is a LAGG #13218
Fixed: Cannot add a QinQ interface to a bridge #14377
Fixed: find_interface_ipv6_ll() can return a VIP instead of the interface address #14392
Fixed: Interface value is not properly validated when submitted on interfaces_gif_edit.php and interfaces_gre_edit.php #14549
Fixed: Primary interface address is incorrectly set to the last address on the interface #14623
Fixed: Link loss causes interfaces configured as Track Interface for IPv6 to lose their IPv4 addresses #14756
Changed: Eliminate direct config access in interfaces.php #14790
Logging
Fixed: Log rotation is not active if the configuration contains an empty <syslog> section or if that section is not present #14517
Fixed: Per-log settings for file size and retention count are not honored #14545
Added: Improve SCTP support in filterlog #14667
Notifications
Added: Allow SMTP notifications from non-root processes #14337
Fixed: PHP error when failing to write config.cache #14432
OpenVPN
Fixed: OpenVPN can select the wrong interface IP address when multiple addresses are present #14646
Changed: Prevent weak SHA1 certificates from being used with OpenVPN clients and servers #14677
Changed: Check for deprecated OpenVPN encryption and digest options on upgrade #14686
Changed: Update OpenVPN to 2.6.7 #14985
Operating System
Added: Method for users to customize shell initialization behavior #14746
Changed: Automatically configure PF states hash table size #14750
Fixed: Panic when pfsync attempts to synchronize states between hosts with different rulesets #14804
PHP Interpreter
Added: Option to configure a custom value for the PHP memory limit #13377
PPP Interfaces
Fixed: PPP interface default username/password are not being populated from provider data on interfaces.php and interfaces_ppps_edit.php #14544
Fixed: getserviceproviders.php does not always validate value of $connection, displays without encoding #14547
PPPoE Server
Fixed: PPPoE Server address input validation is incorrectly allowing IPv6 #13903
Packet Capture
Added: Change default match modifier from “all of” to “any of” #14650
Fixed: packet_capture.php uses count and length values in command execution without validation or encoding #14809
Rules / NAT
Added: Support interface macros in Outbound NAT rules #3288
Fixed: Negating <interface> net when a VIP exists on the interface results in unintended behavior #6799
Added: Option to wait for interface selection before displaying firewall rules #13124
Added: Support interface groups in firewall rule source/destination fields #14448
Fixed: “Convert interface definitions” option is not respected when bulk copying rules #14576
Fixed: Rule separators are ordered incorrectly after removing rules in certain positions #14619
Fixed: Rule separators are hidden when their index is greater than the number of rules #14621
Added: Extend support for SCTP in firewall and NAT rules #14640
Fixed: Separators get shifted when copying firewall rules between interfaces #14691
Fixed: ctype_digit() returns unexpected result for values <= 255 which can break some validation functions/usages #14702
System Logs
Fixed: status_logs_filter_dynamic.php does not encode value of interfacefilter in raw mode #14548
Traffic Graphs
Fixed: PHP Error when viewing Traffic Graphs in iftop mode #14500
Fixed: Traffic graph filters apply incorrectly #14892
Traffic Shaper (ALTQ)
Fixed: Kernel panic when using traffic shaping on a PPPoE interface #14497
Translations
Fixed: Some functions fail if the Language does not exactly match an available Locale #13776
UPnP/NAT-PMP
Fixed: Remove broken stun.sipgate.net from UPnP STUN server list #14673
Upgrade
Fixed: Update check in GUI does not always honor the configured proxy settings #14609
User Manager / Privileges
Fixed: Copy function for User Manager Groups does not work for first group in list #14695
Web Interface
Fixed: Refactor IPsec code using config access functions #13704
Fixed: PHP error in CSRF Magic from invalid time value #14394
Fixed: Breadcrumb path missing on system_register.php #14462
Changed: Prevent weak SHA1 certificates from being used with GUI and Captive Portal #14672
Fixed: status_carp.php and diag_dump_states.php unresponsive with large state tables #14758
Fixed: Logo text is partially rendered when using Compact-RED theme on CE #14807
Fixed: GUI TCP port is not updated in the configuration when saving with the field empty to remove an existing value #14820
Wireless
Fixed: PHP error in handle_wireless_post() when toggling some wireless interface options #14579
pfSense Plusの無料タイプが廃止されて初のアップデートになります
pfSense CEとしては前回が1年半ぶりの更新だったのに対して
今回は2023/06から2023/11と5か月で更新がきました
明らかに格差をつけられていたPlusとCEですが
無料タイプ廃止の影響でCEのリリース体制がひとまず元に戻った形でしょうか
今回の主な変更点はOpenSSL更新とKea導入です
OpenSSL更新は1.x系がEoLになった影響で3.x系へ更新されました
この影響でVPNで使用できる暗号化アルゴリズム・ハッシュアルゴリズムの一部が削除されました
とはいえ弱いアルゴリズムばかりなのでリストを見る限り普通は使わないものばかりで
大半の人には影響はないと思われますが昔からの設定を使いまわしている方は注意してください
影響があるとすれば以前のOpenVPNで使われていたBlowfishぐらいかと思います
次にKea導入に関してですが
pfSenseは今までDHCPサーバにISC DHCPDを使用していましたがEoLになりましたので
ISCが後継ソフトとして開発しているKeaに移行することになりました
ただし現時点ではプレビュー導入という形で完全に置き換えている訳ではありませんので
pfSenseをアップデートしただけであれば今まで通りISC DHCPDが動作することになります
切り替えたい場合はSystem→Advanced→Networkingで手動切替が可能ですが
まだローカルDNSリゾルバなど今まで使用できていた一部機能がまだ使用できない為
あくまでKeaへ移行作業における第1弾といった感じになります
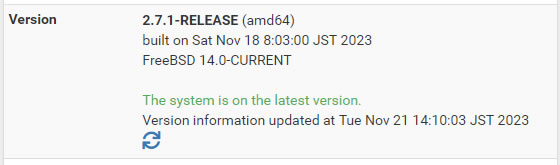
アップデート後、2週間経過してますが特に不具合は発生してません
アップデートの手順
事前に設定のバックアップをした上で以下の操作でアップデートを実行
手順はいつもと同じです
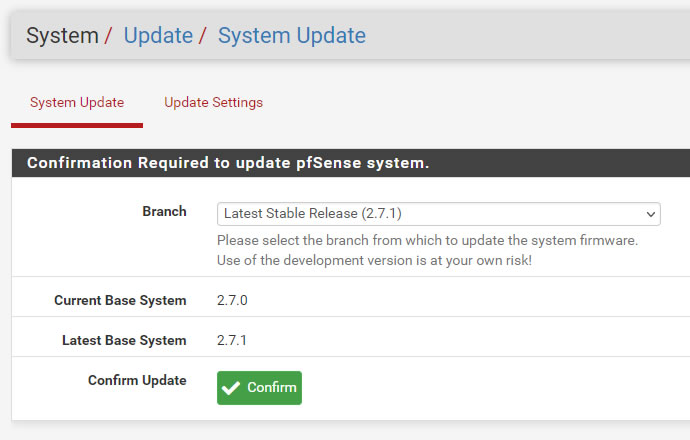
2.7.0から2.7.1へアップデートと表示出てるのを確認して「Confirm」を押す
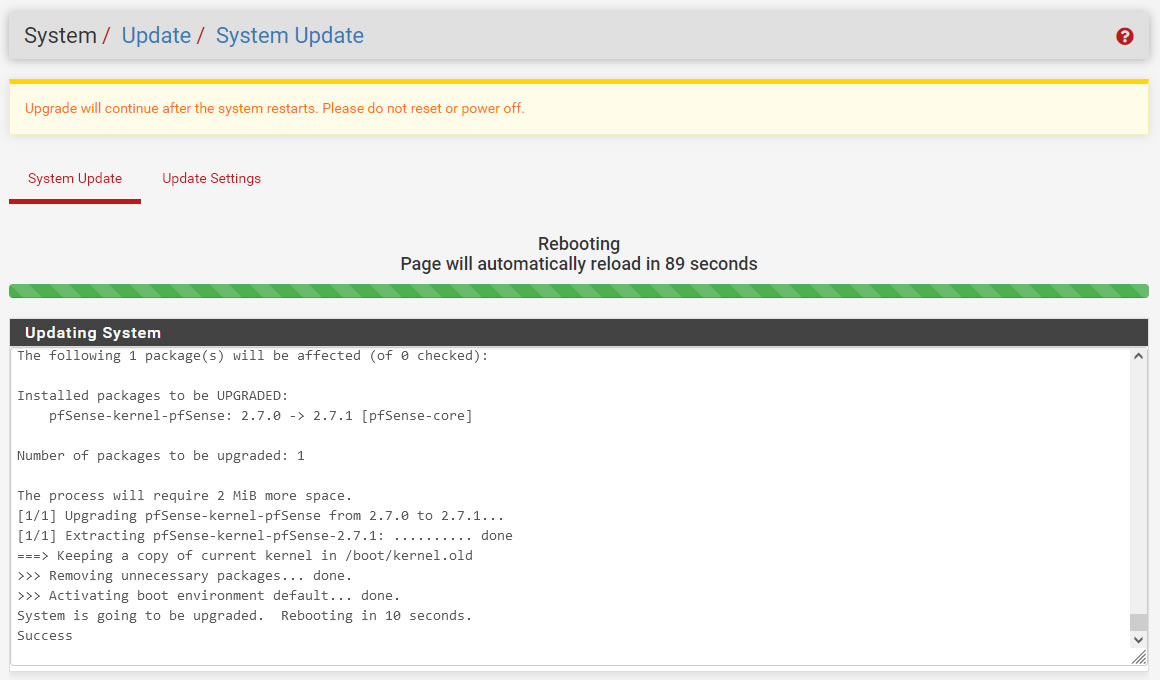
Update時の処理ログ
>>> Updating repositories metadata...
Updating pfSense-core repository catalogue...
Fetching meta.conf: . done
Fetching packagesite.pkg: . done
Processing entries: . done
pfSense-core repository update completed. 4 packages processed.
Updating pfSense repository catalogue...
Fetching meta.conf: . done
Fetching packagesite.pkg: ........ done
Processing entries:
Processing entries............. done
pfSense repository update completed. 549 packages processed.
All repositories are up to date.
>>> Setting vital flag on pkg... done.
>>> Removing vital flag from php82... done.
>>> Downloading upgrade packages...
Updating pfSense-core repository catalogue...
Fetching meta.conf:
Fetching packagesite.pkg:
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
Fetching meta.conf:
Fetching packagesite.pkg:
pfSense repository is up to date.
All repositories are up to date.
Checking for upgrades (82 candidates): .......... done
Processing candidates (82 candidates): .......... done
The following 91 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
boost-libs: 1.83.0 [pfSense]
cpu-microcode-amd: 20230808 [pfSense]
cpu-microcode-intel: 20230808 [pfSense]
cpu-microcode-rc: 1.0 [pfSense]
dhcpcd: 10.0.3 [pfSense]
dhcpleases6: 0.1_3 [pfSense]
kea: 2.4.0_1 [pfSense]
log4cplus: 2.1.0 [pfSense]
pfSense-composer-deps: 0.1 [pfSense]
Installed packages to be UPGRADED:
bind-tools: 9.18.14 -> 9.18.19 [pfSense]
ca_root_nss: 3.89.1 -> 3.93_2 [pfSense]
curl: 8.1.0 -> 8.4.0 [pfSense]
cyrus-sasl: 2.1.28 -> 2.1.28_1 [pfSense]
dbus: 1.14.6,1 -> 1.14.10,1 [pfSense]
devcpu-data: 20230513 -> 20230617_1 [pfSense]
drm-510-kmod: 5.10.163_7 -> 5.10.163_8 [pfSense]
filterlog: 0.1_9 -> 0.1_10 [pfSense]
gettext-runtime: 0.21.1 -> 0.22_1 [pfSense]
glib: 2.76.2,2 -> 2.78.0,2 [pfSense]
gmp: 6.2.1 -> 6.3.0 [pfSense]
hostapd: 2.10_5 -> 2.10_8 [pfSense]
icu: 73.1,1 -> 73.2,1 [pfSense]
isc-dhcp44-relay: 4.4.3P1 -> 4.4.3P1_3 [pfSense]
isc-dhcp44-server: 4.4.3P1 -> 4.4.3P1_3 [pfSense]
json-c: 0.16 -> 0.17 [pfSense]
libedit: 3.1.20221030,1 -> 3.1.20230828,1 [pfSense]
libgcrypt: 1.9.4_1 -> 1.10.2 [pfSense]
libnghttp2: 1.52.0 -> 1.57.0 [pfSense]
libssh2: 1.10.0_1,3 -> 1.11.0_1,3 [pfSense]
libuv: 1.45.0 -> 1.46.0 [pfSense]
libxml2: 2.10.4 -> 2.10.4_1 [pfSense]
links: 2.29,1 -> 2.29_2,1 [pfSense]
lua-resty-core: 0.1.26 -> 0.1.27 [pfSense]
luajit-openresty: 2.1.20230410 -> 2.1.20230911_1 [pfSense]
miniupnpd: 2.3.3,1 -> 2.3.3_1,1 [pfSense]
mobile-broadband-provider-info: 20221107 -> 20230416 [pfSense]
nginx: 1.24.0_6,3 -> 1.24.0_12,3 [pfSense]
ntp: 4.2.8p15_5 -> 4.2.8p17_1 [pfSense]
openldap26-client: 2.6.4 -> 2.6.6 [pfSense]
openvpn: 2.6.4 -> 2.6.7_1 [pfSense]
pcsc-lite: 1.9.9,2 -> 2.0.0,2 [pfSense]
perl5: 5.32.1_3 -> 5.34.1_3 [pfSense]
pfSense: 2.7.0 -> 2.7.1 [pfSense]
pfSense-base: 2.7.0 -> 2.7.1 [pfSense-core]
pfSense-boot: 2.7.0 -> 2.7.1 [pfSense-core]
pfSense-default-config: 2.7.0 -> 2.7.1 [pfSense]
pfSense-kernel-pfSense: 2.7.0 -> 2.7.1 [pfSense-core]
pfSense-repo: 2.7.0 -> 2.7.1 [pfSense]
pftop: 0.8_2 -> 0.8_4 [pfSense]
php82: 8.2.6 -> 8.2.11 [pfSense]
php82-bcmath: 8.2.6 -> 8.2.11 [pfSense]
php82-bz2: 8.2.6 -> 8.2.11 [pfSense]
php82-ctype: 8.2.6 -> 8.2.11 [pfSense]
php82-curl: 8.2.6 -> 8.2.11 [pfSense]
php82-dom: 8.2.6 -> 8.2.11 [pfSense]
php82-filter: 8.2.6 -> 8.2.11 [pfSense]
php82-gettext: 8.2.6 -> 8.2.11 [pfSense]
php82-gmp: 8.2.6 -> 8.2.11 [pfSense]
php82-intl: 8.2.6 -> 8.2.11 [pfSense]
php82-ldap: 8.2.6 -> 8.2.11 [pfSense]
php82-mbstring: 8.2.6 -> 8.2.11 [pfSense]
php82-opcache: 8.2.6 -> 8.2.11 [pfSense]
php82-openssl_x509_crl: 1.3_2 -> 1.3_3 [pfSense]
php82-pcntl: 8.2.6 -> 8.2.11 [pfSense]
php82-pdo: 8.2.6 -> 8.2.11 [pfSense]
php82-pdo_sqlite: 8.2.6 -> 8.2.11 [pfSense]
php82-pear-Mail: 1.4.1,1 -> 1.5.1,1 [pfSense]
php82-posix: 8.2.6 -> 8.2.11 [pfSense]
php82-readline: 8.2.6 -> 8.2.11 [pfSense]
php82-session: 8.2.6 -> 8.2.11 [pfSense]
php82-shmop: 8.2.6 -> 8.2.11 [pfSense]
php82-simplexml: 8.2.6 -> 8.2.11 [pfSense]
php82-sockets: 8.2.6 -> 8.2.11 [pfSense]
php82-sqlite3: 8.2.6 -> 8.2.11 [pfSense]
php82-sysvmsg: 8.2.6 -> 8.2.11 [pfSense]
php82-sysvsem: 8.2.6 -> 8.2.11 [pfSense]
php82-sysvshm: 8.2.6 -> 8.2.11 [pfSense]
php82-tokenizer: 8.2.6 -> 8.2.11 [pfSense]
php82-xml: 8.2.6 -> 8.2.11 [pfSense]
php82-xmlreader: 8.2.6 -> 8.2.11 [pfSense]
php82-xmlwriter: 8.2.6 -> 8.2.11 [pfSense]
php82-zlib: 8.2.6 -> 8.2.11 [pfSense]
python311: 3.11.3 -> 3.11.6 [pfSense]
smartmontools: 7.3 -> 7.4 [pfSense]
sqlite3: 3.41.2,1 -> 3.43.1,1 [pfSense]
strongswan: 5.9.10_2 -> 5.9.11_2 [pfSense]
unbound: 1.17.1_3 -> 1.18.0_1 [pfSense]
voucher: 0.1_2 -> 0.1_3 [pfSense]
wpa_supplicant: 2.10_6 -> 2.10_9 [pfSense]
zstd: 1.5.4_2 -> 1.5.5 [pfSense]
Installed packages to be REINSTALLED:
rrdtool-1.8.0_2 [pfSense] (direct dependency changed: perl5)
Number of packages to be installed: 9
Number of packages to be upgraded: 81
Number of packages to be reinstalled: 1
The process will require 387 MiB more space.
289 MiB to be downloaded.
[1/91] Fetching unbound-1.18.0_1.pkg: .......... done
[2/91] Fetching php82-session-8.2.11.pkg: . done
[3/91] Fetching php82-gmp-8.2.11.pkg: .. done
[4/91] Fetching wpa_supplicant-2.10_9.pkg: .......... done
[5/91] Fetching nginx-1.24.0_12,3.pkg: .......... done
[6/91] Fetching pfSense-base-2.7.1.pkg: .......... done
[7/91] Fetching filterlog-0.1_10.pkg: . done
[8/91] Fetching hostapd-2.10_8.pkg: .......... done
[9/91] Fetching devcpu-data-20230617_1.pkg: . done
[10/91] Fetching libuv-1.46.0.pkg: ........ done
[11/91] Fetching boost-libs-1.83.0.pkg: .......... done
[12/91] Fetching php82-zlib-8.2.11.pkg: . done
[13/91] Fetching cpu-microcode-amd-20230808.pkg: .... done
[14/91] Fetching php82-dom-8.2.11.pkg: ..... done
[15/91] Fetching php82-simplexml-8.2.11.pkg: .. done
[16/91] Fetching json-c-0.17.pkg: ..... done
[17/91] Fetching php82-shmop-8.2.11.pkg: . done
[18/91] Fetching lua-resty-core-0.1.27.pkg: .. done
[19/91] Fetching pcsc-lite-2.0.0,2.pkg: ..... done
[20/91] Fetching openvpn-2.6.7_1.pkg: .......... done
[21/91] Fetching php82-pdo-8.2.11.pkg: .. done
[22/91] Fetching libnghttp2-1.57.0.pkg: ......... done
[23/91] Fetching libxml2-2.10.4_1.pkg: .......... done
[24/91] Fetching php82-readline-8.2.11.pkg: . done
[25/91] Fetching php82-curl-8.2.11.pkg: ... done
[26/91] Fetching icu-73.2,1.pkg: .......... done
[27/91] Fetching pfSense-default-config-2.7.1.pkg: . done
[28/91] Fetching bind-tools-9.18.19.pkg: .......... done
[29/91] Fetching rrdtool-1.8.0_2.pkg: .......... done
[30/91] Fetching pfSense-2.7.1.pkg: .......... done
[31/91] Fetching php82-mbstring-8.2.11.pkg: .......... done
[32/91] Fetching isc-dhcp44-server-4.4.3P1_3.pkg: .......... done
[33/91] Fetching php82-tokenizer-8.2.11.pkg: . done
[34/91] Fetching ntp-4.2.8p17_1.pkg: .......... done
[35/91] Fetching voucher-0.1_3.pkg: . done
[36/91] Fetching php82-ldap-8.2.11.pkg: .. done
[37/91] Fetching pfSense-boot-2.7.1.pkg: .......... done
[38/91] Fetching miniupnpd-2.3.3_1,1.pkg: .... done
[39/91] Fetching ca_root_nss-3.93_2.pkg: .......... done
[40/91] Fetching drm-510-kmod-5.10.163_8.pkg: .......... done
[41/91] Fetching python311-3.11.6.pkg: .......... done
[42/91] Fetching links-2.29_2,1.pkg: .......... done
[43/91] Fetching pfSense-repo-2.7.1.pkg: . done
[44/91] Fetching php82-sysvmsg-8.2.11.pkg: . done
[45/91] Fetching kea-2.4.0_1.pkg: .......... done
[46/91] Fetching dhcpcd-10.0.3.pkg: ......... done
[47/91] Fetching dbus-1.14.10,1.pkg: .......... done
[48/91] Fetching libedit-3.1.20230828,1.pkg: ....... done
[49/91] Fetching pfSense-composer-deps-0.1.pkg: .......... done
[50/91] Fetching mobile-broadband-provider-info-20230416.pkg: ... done
[51/91] Fetching php82-posix-8.2.11.pkg: . done
[52/91] Fetching dhcpleases6-0.1_3.pkg: . done
[53/91] Fetching libgcrypt-1.10.2.pkg: .......... done
[54/91] Fetching php82-sockets-8.2.11.pkg: .. done
[55/91] Fetching php82-8.2.11.pkg: .......... done
[56/91] Fetching php82-sqlite3-8.2.11.pkg: .. done
[57/91] Fetching pfSense-kernel-pfSense-2.7.1.pkg: .......... done
[58/91] Fetching zstd-1.5.5.pkg: .......... done
[59/91] Fetching php82-xmlreader-8.2.11.pkg: . done
[60/91] Fetching log4cplus-2.1.0.pkg: ...... done
[61/91] Fetching php82-pcntl-8.2.11.pkg: .. done
[62/91] Fetching php82-xml-8.2.11.pkg: .. done
[63/91] Fetching curl-8.4.0.pkg: .......... done
[64/91] Fetching gmp-6.3.0.pkg: .......... done
[65/91] Fetching gettext-runtime-0.22_1.pkg: .......... done
[66/91] Fetching php82-intl-8.2.11.pkg: .......... done
[67/91] Fetching php82-bcmath-8.2.11.pkg: . done
[68/91] Fetching php82-bz2-8.2.11.pkg: . done
[69/91] Fetching cyrus-sasl-2.1.28_1.pkg: .......... done
[70/91] Fetching php82-openssl_x509_crl-1.3_3.pkg: . done
[71/91] Fetching php82-sysvshm-8.2.11.pkg: . done
[72/91] Fetching php82-xmlwriter-8.2.11.pkg: . done
[73/91] Fetching sqlite3-3.43.1,1.pkg: .......... done
[74/91] Fetching php82-gettext-8.2.11.pkg: . done
[75/91] Fetching openldap26-client-2.6.6.pkg: .......... done
[76/91] Fetching glib-2.78.0,2.pkg: .......... done
[77/91] Fetching cpu-microcode-rc-1.0.pkg: . done
[78/91] Fetching luajit-openresty-2.1.20230911_1.pkg: .......... done
[79/91] Fetching perl5-5.34.1_3.pkg: .......... done
[80/91] Fetching strongswan-5.9.11_2.pkg: .......... done
[81/91] Fetching php82-sysvsem-8.2.11.pkg: . done
[82/91] Fetching php82-pear-Mail-1.5.1,1.pkg: . done
[83/91] Fetching php82-ctype-8.2.11.pkg: . done
[84/91] Fetching smartmontools-7.4.pkg: .......... done
[85/91] Fetching libssh2-1.11.0_1,3.pkg: .......... done
[86/91] Fetching cpu-microcode-intel-20230808.pkg: .......... done
[87/91] Fetching isc-dhcp44-relay-4.4.3P1_3.pkg: .......... done
[88/91] Fetching php82-opcache-8.2.11.pkg: .......... done
[89/91] Fetching pftop-0.8_4.pkg: .... done
[90/91] Fetching php82-filter-8.2.11.pkg: . done
[91/91] Fetching php82-pdo_sqlite-8.2.11.pkg: . done
Checking integrity... done (4 conflicting)
- cpu-microcode-amd-20230808 [pfSense] conflicts with devcpu-data-amd-20230424 [installed] on /usr/local/share/cpucontrol/microcode_amd.bin
- pfSense-2.7.1 [pfSense] conflicts with pfSense-rc-2.7.0 [installed] on /etc/pfSense-rc
- cpu-microcode-rc-1.0 [pfSense] conflicts with devcpu-data-20230513 [installed] on /usr/local/etc/rc.d/microcode_update
- cpu-microcode-intel-20230808 [pfSense] conflicts with devcpu-data-intel-20230512 [installed] on /usr/local/share/cpucontrol/06-03-02.00
Checking integrity... done (0 conflicting)
Conflicts with the existing packages have been found.
One more solver iteration is needed to resolve them.
The following 95 package(s) will be affected (of 0 checked):
Installed packages to be REMOVED:
devcpu-data-amd: 20230424
devcpu-data-intel: 20230512
pfSense-rc: 2.7.0
New packages to be INSTALLED:
boost-libs: 1.83.0 [pfSense]
cpu-microcode-amd: 20230808 [pfSense]
cpu-microcode-intel: 20230808 [pfSense]
cpu-microcode-rc: 1.0 [pfSense]
dhcpcd: 10.0.3 [pfSense]
dhcpleases6: 0.1_3 [pfSense]
kea: 2.4.0_1 [pfSense]
log4cplus: 2.1.0 [pfSense]
pfSense-composer-deps: 0.1 [pfSense]
Installed packages to be UPGRADED:
bind-tools: 9.18.14 -> 9.18.19 [pfSense]
ca_root_nss: 3.89.1 -> 3.93_2 [pfSense]
curl: 8.1.0 -> 8.4.0 [pfSense]
cyrus-sasl: 2.1.28 -> 2.1.28_1 [pfSense]
dbus: 1.14.6,1 -> 1.14.10,1 [pfSense]
drm-510-kmod: 5.10.163_7 -> 5.10.163_8 [pfSense]
filterlog: 0.1_9 -> 0.1_10 [pfSense]
gettext-runtime: 0.21.1 -> 0.22_1 [pfSense]
glib: 2.76.2,2 -> 2.78.0,2 [pfSense]
gmp: 6.2.1 -> 6.3.0 [pfSense]
hostapd: 2.10_5 -> 2.10_8 [pfSense]
icu: 73.1,1 -> 73.2,1 [pfSense]
isc-dhcp44-relay: 4.4.3P1 -> 4.4.3P1_3 [pfSense]
isc-dhcp44-server: 4.4.3P1 -> 4.4.3P1_3 [pfSense]
json-c: 0.16 -> 0.17 [pfSense]
libedit: 3.1.20221030,1 -> 3.1.20230828,1 [pfSense]
libgcrypt: 1.9.4_1 -> 1.10.2 [pfSense]
libnghttp2: 1.52.0 -> 1.57.0 [pfSense]
libssh2: 1.10.0_1,3 -> 1.11.0_1,3 [pfSense]
libuv: 1.45.0 -> 1.46.0 [pfSense]
libxml2: 2.10.4 -> 2.10.4_1 [pfSense]
links: 2.29,1 -> 2.29_2,1 [pfSense]
lua-resty-core: 0.1.26 -> 0.1.27 [pfSense]
luajit-openresty: 2.1.20230410 -> 2.1.20230911_1 [pfSense]
miniupnpd: 2.3.3,1 -> 2.3.3_1,1 [pfSense]
mobile-broadband-provider-info: 20221107 -> 20230416 [pfSense]
nginx: 1.24.0_6,3 -> 1.24.0_12,3 [pfSense]
ntp: 4.2.8p15_5 -> 4.2.8p17_1 [pfSense]
openldap26-client: 2.6.4 -> 2.6.6 [pfSense]
openvpn: 2.6.4 -> 2.6.7_1 [pfSense]
pcsc-lite: 1.9.9,2 -> 2.0.0,2 [pfSense]
perl5: 5.32.1_3 -> 5.34.1_3 [pfSense]
pfSense: 2.7.0 -> 2.7.1 [pfSense]
pfSense-base: 2.7.0 -> 2.7.1 [pfSense-core]
pfSense-boot: 2.7.0 -> 2.7.1 [pfSense-core]
pfSense-default-config: 2.7.0 -> 2.7.1 [pfSense]
pfSense-kernel-pfSense: 2.7.0 -> 2.7.1 [pfSense-core]
pfSense-repo: 2.7.0 -> 2.7.1 [pfSense]
pftop: 0.8_2 -> 0.8_4 [pfSense]
php82: 8.2.6 -> 8.2.11 [pfSense]
php82-bcmath: 8.2.6 -> 8.2.11 [pfSense]
php82-bz2: 8.2.6 -> 8.2.11 [pfSense]
php82-ctype: 8.2.6 -> 8.2.11 [pfSense]
php82-curl: 8.2.6 -> 8.2.11 [pfSense]
php82-dom: 8.2.6 -> 8.2.11 [pfSense]
php82-filter: 8.2.6 -> 8.2.11 [pfSense]
php82-gettext: 8.2.6 -> 8.2.11 [pfSense]
php82-gmp: 8.2.6 -> 8.2.11 [pfSense]
php82-intl: 8.2.6 -> 8.2.11 [pfSense]
php82-ldap: 8.2.6 -> 8.2.11 [pfSense]
php82-mbstring: 8.2.6 -> 8.2.11 [pfSense]
php82-opcache: 8.2.6 -> 8.2.11 [pfSense]
php82-openssl_x509_crl: 1.3_2 -> 1.3_3 [pfSense]
php82-pcntl: 8.2.6 -> 8.2.11 [pfSense]
php82-pdo: 8.2.6 -> 8.2.11 [pfSense]
php82-pdo_sqlite: 8.2.6 -> 8.2.11 [pfSense]
php82-pear-Mail: 1.4.1,1 -> 1.5.1,1 [pfSense]
php82-posix: 8.2.6 -> 8.2.11 [pfSense]
php82-readline: 8.2.6 -> 8.2.11 [pfSense]
php82-session: 8.2.6 -> 8.2.11 [pfSense]
php82-shmop: 8.2.6 -> 8.2.11 [pfSense]
php82-simplexml: 8.2.6 -> 8.2.11 [pfSense]
php82-sockets: 8.2.6 -> 8.2.11 [pfSense]
php82-sqlite3: 8.2.6 -> 8.2.11 [pfSense]
php82-sysvmsg: 8.2.6 -> 8.2.11 [pfSense]
php82-sysvsem: 8.2.6 -> 8.2.11 [pfSense]
php82-sysvshm: 8.2.6 -> 8.2.11 [pfSense]
php82-tokenizer: 8.2.6 -> 8.2.11 [pfSense]
php82-xml: 8.2.6 -> 8.2.11 [pfSense]
php82-xmlreader: 8.2.6 -> 8.2.11 [pfSense]
php82-xmlwriter: 8.2.6 -> 8.2.11 [pfSense]
php82-zlib: 8.2.6 -> 8.2.11 [pfSense]
python311: 3.11.3 -> 3.11.6 [pfSense]
smartmontools: 7.3 -> 7.4 [pfSense]
sqlite3: 3.41.2,1 -> 3.43.1,1 [pfSense]
strongswan: 5.9.10_2 -> 5.9.11_2 [pfSense]
unbound: 1.17.1_3 -> 1.18.0_1 [pfSense]
voucher: 0.1_2 -> 0.1_3 [pfSense]
wpa_supplicant: 2.10_6 -> 2.10_9 [pfSense]
zstd: 1.5.4_2 -> 1.5.5 [pfSense]
Installed packages to be REINSTALLED:
rrdtool-1.8.0_2 [pfSense] (direct dependency changed: perl5)
Number of packages to be removed: 3
Number of packages to be installed: 9
Number of packages to be upgraded: 80
Number of packages to be reinstalled: 1
The process will require 368 MiB more space.
>>> Downloading pkg...
No packages are required to be fetched.
Integrity check was successful.
>>> Upgrading pfSense-boot...>>> Unmounting /boot/efi... done.
Updating pfSense-core repository catalogue...
Fetching meta.conf:
Fetching packagesite.pkg:
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
Fetching meta.conf:
Fetching packagesite.pkg:
pfSense repository is up to date.
All repositories are up to date.
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pfSense-boot: 2.7.0 -> 2.7.1 [pfSense-core]
Number of packages to be upgraded: 1
[1/1] Upgrading pfSense-boot from 2.7.0 to 2.7.1...
[1/1] Extracting pfSense-boot-2.7.1: .......... done
>>> Removing vital flag from pfSense-rc... done.
>>> Upgrading pfSense kernel...
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pfSense-kernel-pfSense: 2.7.0 -> 2.7.1 [pfSense-core]
Number of packages to be upgraded: 1
The process will require 2 MiB more space.
[1/1] Upgrading pfSense-kernel-pfSense from 2.7.0 to 2.7.1...
[1/1] Extracting pfSense-kernel-pfSense-2.7.1: .......... done
===> Keeping a copy of current kernel in /boot/kernel.old
>>> Removing unnecessary packages... done.
>>> Activating boot environment default... done.
System is going to be upgraded. Rebooting in 10 seconds.
Success


コメント