Mikrotik RouterOSをアップデートした記録 6.42.6→6.42.7
アップデート内容確認
MikrotikのRouterOSを
6.42.6から6.42.7にWinboxを使ってアップデートします
変更点の確認はこちら
MikroTik Routers and Wireless – Software
https://mikrotik.com/download/changelogs
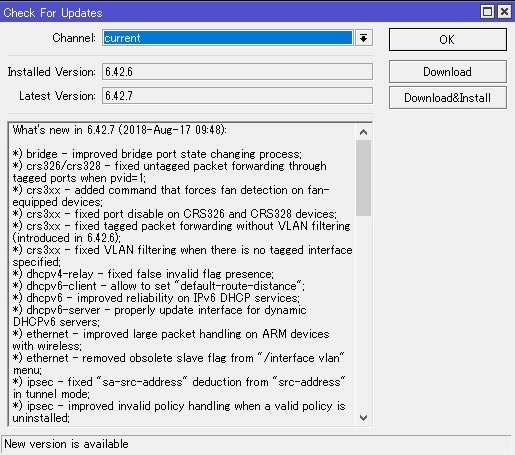
What's new in 6.42.7 (2018-Aug-17 09:48): MAJOR CHANGES IN v6.42.7: ---------------------- !) security - fixed vulnerabilities CVE-2018-1156, CVE-2018-1157, CVE-2018-1158, CVE-2018-1159; ---------------------- *) bridge - improved bridge port state changing process; *) crs326/crs328 - fixed untagged packet forwarding through tagged ports when pvid=1; *) crs3xx - added command that forces fan detection on fan-equipped devices; *) crs3xx - fixed port disable on CRS326 and CRS328 devices; *) crs3xx - fixed tagged packet forwarding without VLAN filtering (introduced in 6.42.6); *) crs3xx - fixed VLAN filtering when there is no tagged interface specified; *) dhcpv4-relay - fixed false invalid flag presence; *) dhcpv6-client - allow to set "default-route-distance"; *) dhcpv6 - improved reliability on IPv6 DHCP services; *) dhcpv6-server - properly update interface for dynamic DHCPv6 servers; *) ethernet - improved large packet handling on ARM devices with wireless; *) ethernet - removed obsolete slave flag from "/interface vlan" menu; *) ipsec - fixed "sa-src-address" deduction from "src-address" in tunnel mode; *) ipsec - improved invalid policy handling when a valid policy is uninstalled; *) ldp - properly load LDP configuration; *) led - fixed default LED configuration for RBLHGG-5acD-XL devices; *) lte - added signal readings under "/interface lte scan" for 3G and GSM modes; *) lte - fixed memory leak on USB disconnect; *) lte - fixed SMS send feature when not in LTE network; *) package - do not allow to install out of bundle package if it already exists within bundle; *) ppp - fixed interface enabling after a while if none of them where active; *) sfp - hide "sfp-wavelength" parameter for RJ45 transceivers; *) tr069-client - fixed unresponsive tr069 service when blackhole route is present; *) upgrade - fixed RouterOS upgrade process from RouterOS v5; *) userman - fixed compatibility with PayPal TLS 1.2; *) vrrp - fixed VRRP packet processing on VirtualBox and VMWare hypervisors; *) w60g - added distance measurement feature; *) w60g - fixed random disconnects; *) w60g - general stability and performance improvements; *) w60g - improved MCS rate detection process; *) w60g - improved MTU change handling; *) w60g - properly close connection with station on disconnect; *) w60g - stop doing distance measurements after first successful measurement; *) winbox - added "secondary-channel" setting to wireless interface if 80 MHz mode is selected; *) winbox - fixed "sfp-connector-type" value presence under "Interface/Ethernet"; *) winbox - fixed warning presence for "IP/IPsec/Peers" menu; *) winbox - properly display all flags for bridge host entries; *) winbox - show "System/RouterBOARD/Mode Button" on devices that has such feature; *) wireless - added option to disable PMKID for WPA2; *) wireless - fixed memory leak when performing wireless scan on ARM; *) wireless - fixed packet processing after removing wireless interface from CAP settings; *) wireless - updated "united-states" regulatory domain information;
不具合修正と一部デバイスの最適化って感じです
所要時間は5分程度
2018/08/22 追記
当初記載はなかったのですが
CVE-2018-1156, CVE-2018-1157, CVE-2018-1158, CVE-2018-1159が
修正されていた模様です
CVE IDで検索しても現時点ではまだ情報公開されていませんでしたので
詳細は不明ですが迅速にアプデ対応をしておいた方がいいかと思われます
2018/08/23 追記
CVE-2018-1156, CVE-2018-1157, CVE-2018-1158, CVE-2018-1159の詳細が出てました
ユーザ認証を超える必要があるので外部から云々の問題ではないようです
MikroTik blog – Security issues discovered by Tenable
https://blog.mikrotik.com/security/security-issues-discovered-by-tenable.html
CVE-2018-1156: An authenticated user can trigger a stack buffer overflow.
CVE-2018-1157: File upload memory exhaustion. An authenticated user can cause the www binary to consume all memory.
CVE-2018-1158: Recursive JSON parsing stack exhaustion, which could allow an authenticated user to cause crash of the www service.
CVE-2018-1159: www memory corruption, if connections are initiated and not properly cleaned up then a heap corruption occurs in www.
アップデートの手順
事前にバックアップをした上で以下の操作でアップデートを実行
RouterOSのアップデート
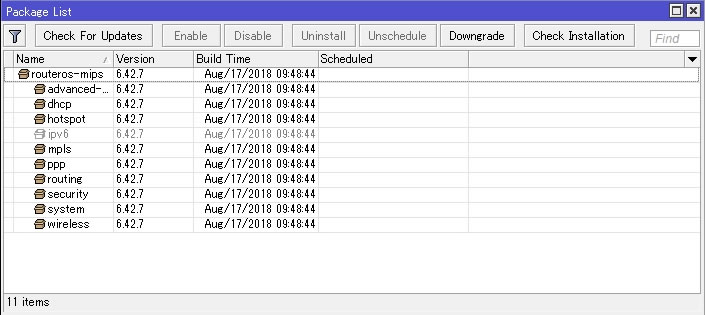
System→PackagesでPackage Listを開いて左上の「Check For Updates」を選択

6.42.6から6.42.7へアップデートと表示出てるのを確認して「Download&Install」を押す
無事に完了すると自動で再起動開始されます
再起動後にPackage ListにてVersionが6.42.7になっているのを確認
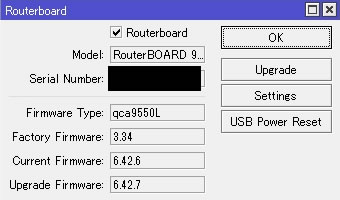
FWのアップデート
FW更新を行うためSystem→Routerboardを開く
Upgrade Firmwareが6.42.7になっているのを確認して「Upgrade」ボタンを選択
確認画面を経て更新完了すれば以下メッセージが表示される
”Firmware upgraded successfully. please reboot for changes to take effect!”
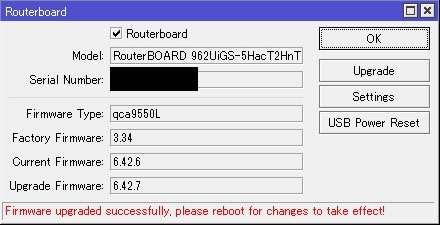
指示通りSystem→Rebootから再起動
再起動後にSystem→RouterboardにてCurrent Firmwareが6.42.7になっているのを確認
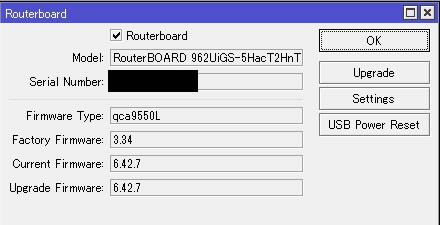
最後に最新Verの状態でバックアップをして完了


コメント