pfSenseをアップデートした記録 2.4.5→2.4.5_1
アップデート内容確認
2.4.5から2.4.5_1(2.4.5-p1)にアップデートします
変更点を確認
https://docs.netgate.com/pfsense/en/latest/releases/2-4-5-p1-new-features-and-changes.html
Security / Errata
Addressed an issue with large pf tables causing system instability and high CPU usage during filter reload events #10414
Fixed an issue with sshguard which could prevent it from protecting against brute force logins #10488
Updated unbound to address CVE-2020-12662 and CVE-2020-12663 #10576
Updated json-c to address CVE-2020-12762 #10609
Addressed FreeBSD Security Advisories & Errata Notices including:
FreeBSD-SA-20:10.ipfw
FreeBSD-SA-20:12.libalias
FreeBSD-SA-20:13.libalias
FreeBSD-SA-20:15.cryptodev
Aliases / Tables
Fixed handling of URL/URL table aliases with IDN hostnames #10321
Authentication
Fixed handling of misconfigured groups which prevented the admin user from making configuration changes #10492
Fixed a potential temporary privilege downgrade when deleting an account #9259
Backup / Restore
Fixed handling of redundant/extraneous RRD tags when making configuration backups #10508
CARP
Fixed handling of IPv6 CARP VIPs with non-significant zeros during XMLRPC sync #6579
Certificates
Fixed a bug which prevented the user from removing a CA private key when editing #10509
Configuration Upgrade
Fixed a PHP error during upgrade from <2.4.3 with empty tags in the IPsec configuration #10458
Console Menu
Changed the naming convention of gateways created at the console to be the same as those created in the GUI #10264
DHCP (IPv6)
Added default value placeholders to some DHCPv6 RA configuration options #10448
Fixed DHCPv6 service Dynamic DNS errors #10346
Fixed rc.newwanipv6 being called for Request messages which dhcp6c should have discarded #9634
Added dashed DUID support to DHCPv6 static mappings #2568
DHCP Relay
Fixed DHCP Relay handling of scenarios where a target server may be on the same interface as some clients #10416
Excluded unsupported interface types from DHCP Relay #10341
DHCP Server
Fixed DHCPv6 static entries not being updated on external Dynamic DNS servers #10412
Fixed DHCPv6 domain-search list not being sent to clients #10200
Fixed DHCP Server not accepting IPv6 addresses for Dynamic DNS servers #6600
Diagnostics
Several improvements and items added to status.php diagnostic output #10455 #10424 #10423 #10350 #10349 #10568
Fixed Require State Filter setting on diag_states.php breaking filter rule link to associated states #10359
DNS Resolver
Fixed IPsec and OpenVPN IPv6 tunnel network/pool prefixes not being added to automatic DNS Resolver ACLs #10460
Fixed EDNS buffer size values to prepare for 2020 DNS flag day #10293
Fixed DNS Resolver handling of entries from DHCP server which contain a trailing dot in domain names #8054
Dynamic DNS
Fixed DigitalOcean Dynamic DNS client handling of IPv6 addresses #10390
Fixed DNSExit update URL #9632
Hardware / Drivers
Added support for iwm devices #7725
Note:This device only supports Station mode. It does not support acting as an access point.
Added ng_etf module to armv6 and aarch64 kernels #10463
Added QLogic 10G driver (qlxgb/qla80xx) #9891
Added virtio_console to the kernel #9985
IPsec
Fixed selection of IPsec VTI Phase 2 local network address/mask values #10418
Fixed saving IPsec connection breaking FRR BGP on VTI interfaces #10351
Updated DH group warnings to say that group 5 is also weak #10221
Fixed disabling IPsec Phase 1 with a VTI Phase 2 #10190
Fixed disabled IPsec Phase 2 entries being unintentionally included in vpn_networks table #7622
L2TP
Changed L2TP mpd.secret handling so that the server is not restarted after adding/modifying L2TP users #4866
Fixed handling of L2TP usernames containing a realm separator (@) #9828
Fixed Shared Secret handling in L2TP #10531 #10527
Limiters
Fixed input validation of limiters with ECN #10211
Fixed bogus extra warning dialog on when deleting limiters #9334
Notifications
Fixed SMTP notification SSL validation to respect the user-selected behavior #10317
NTPD
Added localhost to NTP Interface selection options #10348
OpenVPN
Fixed OpenVPN remote statement protocol handling #10368
Added option to configure OpenVPN username as common name behavior #8289
Operating System
Fixed handling of RAM disk sizes not accounting for existing disk usage when calculating available kernel memory, which could prevent saving #10420
Updated pkg to 1.13.x #10564
Fixed problems preventing the Netgate Coreboot Package from updating Coreboot properly #10573
Packages
Fixed handling of FreeRADIUS passwords containing non-XML-safe characters #4497
Fixed handling of Squid LDAP search filters containing an accent #7654
Fixed issues preventing FRR from working on certain platforms such as SG-1100 (arm64/aarch64) #10444
Fixed issues preventing Suricata from working on certain platforms such as SG-1100 (arm64/aarch64) #10228
Rules / NAT
Fixed Duplicate Outbound NAT entries from L2TP server addresses #10247
Fixed Outbound NAT rules for mobile IPsec users with per-user addresses defined #9320
Fixed IPv6 IP Alias VIPs not being added to Interface Network macros #8256
Fixed Destination port range “Any” in Port Forward rules #7704
Fixed display of interfaces on the Floating rules list #4629
Fixed rule description validation to reject \ #10542
Fixed setting NAT reflection timeout values #10591
Translations
Fixed language selection for Chinese (Taiwan) / HK Translations #10525
Services
Fixed is_process_running() handling of empty process, which could lead to an error when using the CLI to query the status of a service which does not exist #10540
Web Interface
Fixed dark theme auto-complete popup field having dark text on dark background #10499
Fixed using special characters in Schedule descriptions #10305
Fixed WebGUI main page loading very slowly when there is no Internet connectivity #8987
p1ということで脆弱性対応がメインです
アップデートの手順
事前に設定のバックアップをした上で以下の操作でアップデートを実行
手順はいつもと同じです
まずダッシュボードのVersionのところにある雲マークか
System→Updateを選択
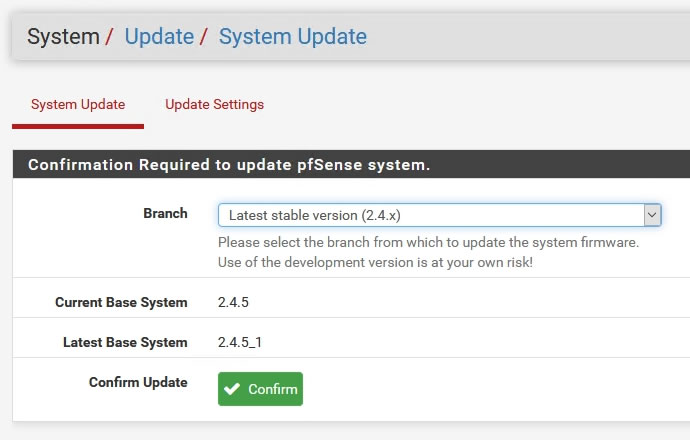
2.4.5から2.4.5_1へアップデートと表示出てるのを確認して「Confirm」を押す
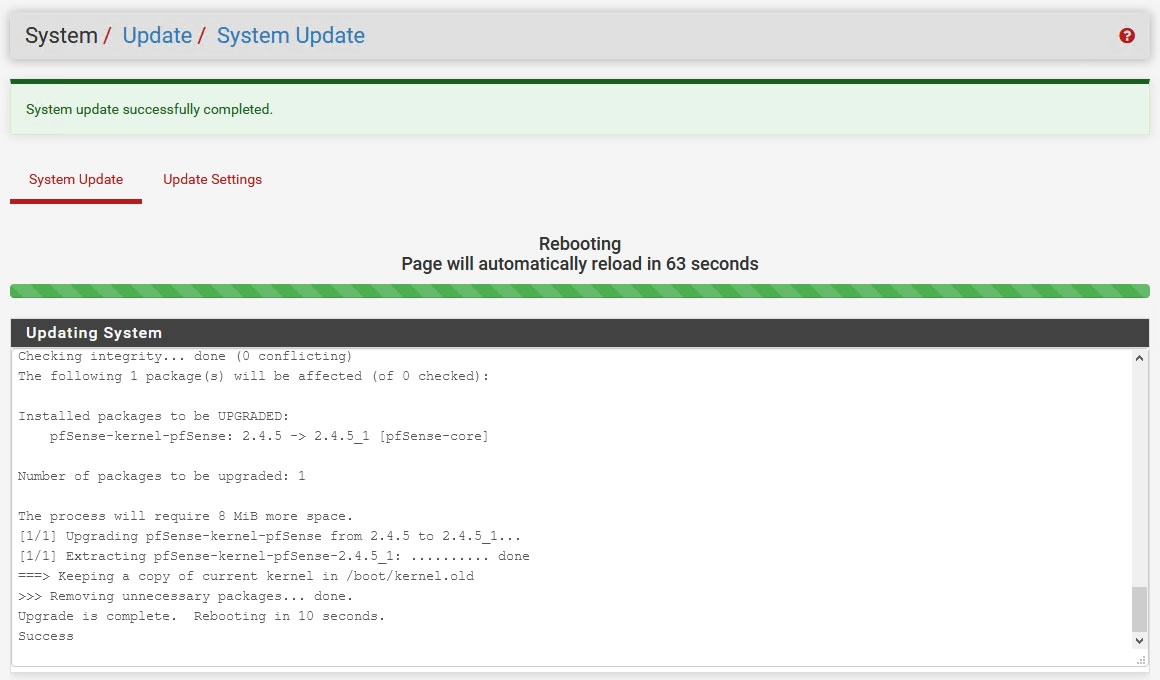
Update時の処理ログ
>>> Updating repositories metadata...
Updating pfSense-core repository catalogue...
Fetching meta.txz: . done
Fetching packagesite.txz: . done
Processing entries: . done
pfSense-core repository update completed. 7 packages processed.
Updating pfSense repository catalogue...
Fetching meta.conf: . done
Fetching packagesite.txz: .......... done
Processing entries: .......... done
pfSense repository update completed. 521 packages processed.
All repositories are up to date.
>>> Setting vital flag on pkg... done.
>>> Removing vital flag from php72... done.
>>> Downloading upgrade packages...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Checking for upgrades (12 candidates): .......... done
Processing candidates (12 candidates): .......... done
The following 12 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
bind-tools: 9.14.9 -> 9.14.12 [pfSense]
json-c: 0.13.1_1 -> 0.14 [pfSense]
openvpn: 2.4.8 -> 2.4.9 [pfSense]
pfSense: 2.4.5 -> 2.4.5_1 [pfSense]
pfSense-base: 2.4.5 -> 2.4.5_1 [pfSense-core]
pfSense-default-config: 2.4.5 -> 2.4.5_1 [pfSense-core]
pfSense-kernel-pfSense: 2.4.5 -> 2.4.5_1 [pfSense-core]
pfSense-rc: 2.4.5 -> 2.4.5_1 [pfSense-core]
python37: 3.7.6 -> 3.7.7 [pfSense]
sshguard: 2.4.0_3,1 -> 2.4.0_4,1 [pfSense]
strongswan: 5.8.2 -> 5.8.4 [pfSense]
unbound: 1.9.6 -> 1.10.1 [pfSense]
Number of packages to be upgraded: 12
The process will require 9 MiB more space.
78 MiB to be downloaded.
[1/12] Fetching unbound-1.10.1.txz: .......... done
[2/12] Fetching strongswan-5.8.4.txz: .......... done
[3/12] Fetching sshguard-2.4.0_4,1.txz: .......... done
[4/12] Fetching python37-3.7.7.txz: .......... done
[5/12] Fetching pfSense-rc-2.4.5_1.txz: .. done
[6/12] Fetching pfSense-kernel-pfSense-2.4.5_1.txz: .......... done
[7/12] Fetching pfSense-default-config-2.4.5_1.txz: . done
[8/12] Fetching pfSense-base-2.4.5_1.txz: .......... done
[9/12] Fetching pfSense-2.4.5_1.txz: . done
[10/12] Fetching openvpn-2.4.9.txz: .......... done
[11/12] Fetching json-c-0.14.txz: ......... done
[12/12] Fetching bind-tools-9.14.12.txz: .......... done
Checking integrity... done (0 conflicting)
>>> Upgrading pfSense-rc...
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pfSense-rc: 2.4.5 -> 2.4.5_1 [pfSense-core]
Number of packages to be upgraded: 1
[1/1] Upgrading pfSense-rc from 2.4.5 to 2.4.5_1...
[1/1] Extracting pfSense-rc-2.4.5_1: ...... done
>>> Upgrading pfSense kernel...
Checking integrity... done (0 conflicting)
The following 1 package(s) will be affected (of 0 checked):
Installed packages to be UPGRADED:
pfSense-kernel-pfSense: 2.4.5 -> 2.4.5_1 [pfSense-core]
Number of packages to be upgraded: 1
The process will require 8 MiB more space.
[1/1] Upgrading pfSense-kernel-pfSense from 2.4.5 to 2.4.5_1...
[1/1] Extracting pfSense-kernel-pfSense-2.4.5_1: .......... done
===> Keeping a copy of current kernel in /boot/kernel.old
>>> Removing unnecessary packages... done.
Upgrade is complete. Rebooting in 10 seconds.
Success



コメント